I’m a Ukrainian student and a unix/linux & open-source enthusiast
Specialized in Cybersecurity, Penetration Testing, Red-Teaming, Bug-Bounty hunting
My skills are:
- Cybersecurity
- Penetration testing
- Low-level programming: C/C++, Assembly (RISC-V, x86-64, ARM),
- Malware analysis/development
- Reverse engineering (IDA, Ghidra, Binary Ninja)
- Self-hosting
- DevOps
- A little bit of 3D (Blender)
- A little bit of game development (Unity, UE5)
Cybersecurity
I’ve been into cybersecurity for about ~2.5 years now.
Familiar with such frameworks: SOC 2, ISO 27001, OWASP top 10, HIPAA, PCI DSS, GDPR, NIST CSF.
Have basic understanding of OWASP ASVS (security standard for web apps) and OWASP WSTG (testing guide).
Have hands-on experience with web Penetration Testing, Unix/Windows systems exploitation.
Wrote my own writeups on CTFs: Environment machine on HTB.
Have some experience with writing security audits/reports for non-technical audience.
Know and use in practice many different tools/techniques for tests, favorite ones:
- Reconnaissance: amass, ffuf, subfinder, httpx, dnsx, gobuster, dirsearch etc.
- Web pentest: Burp Suite, Caido, OWASP ZAP, ffuf, curl, intersect, manual scripting (with python/bash)
- Lateral movement: Impacket (Windows), linPEAS (Linux), BloodHound, netcat, chisel, built-in windows/linux tools.
- Reverse engineering & Binary exploitation: mainly Ghidra, radare2, gdb, IDA Pro, strace, strings etc.
- Persistence: gsocket, segfault (thc.org), process hiding etc.
There's still big room to improve since there's insane amount of different fields to explore in cybersecurity and that's what I'm trying to do.
HackTheBox
My HTB profile
As of right now I’ve solved more than 50 boxes (4 of them “Insane”: DarkCorp, Mist, MassGarden and Cobblestone).
Recently started to write my own writeups on different boxes and challenges.
I like to solve different challenges there, especially reverse engineering, web and pwn.
Some projects I have
Facinus
RepoSince our college switched from Windows to Ubuntu, I had a cool idea to remotely control my classroom PCs.
I discovered gsocket.io and started developing a tool that deploys a local web admin panel to collect logs from connected clients.
I used an Ubuntu VM in QEMU and Bash scripted everything.
OS-in-1000-lines
My implementation of Operating System in 1000 lines by Seiya Nuta.
A small operating system written from scratch for RISC-V CPU architecture.
This project will have basic context switching, paging, user mode, a command-line shell, a disk device driver, and file read/write operations in C.
And also I'll try to add some more functionality to it.
Right now I'm still working on basic stuff before implementing something new.
I'm still learning C and Assembly, the RISC-V instruction set is new to me.
Reverse engineering book translation
This is a book from @mytechnotalent (English version here) that I decided would be cool to translate in Ukrainian with python script and LLM hosted locally
I generally moved from outdated gitbook to honkit for publishing this as an E-book, created a python script for parsing markdown files and translating using LTEngine and Llama LLM (8b params) hosted locally.
I was also able to make an automatic push to my github pages on each update
Bug bounty
Bug bounty is fascinating — legally hacking in-scope apps and possibly earning money.
But it's a hard 'entry point' for beginners. Whole process can be very time-consuming sometimes, and rewards don’t always justify the effort unless you're really skilled.
But there is a big amount of knowledge I'm gaining, when exploring all the different approaches these companies use to secure themselves. It doesn't always bring financial benefits, but it always provides practical experience working with real targets.
I like to compare bug-bounty to a chess game: you have several 'openings' but when digging, you open more available steps to play around.
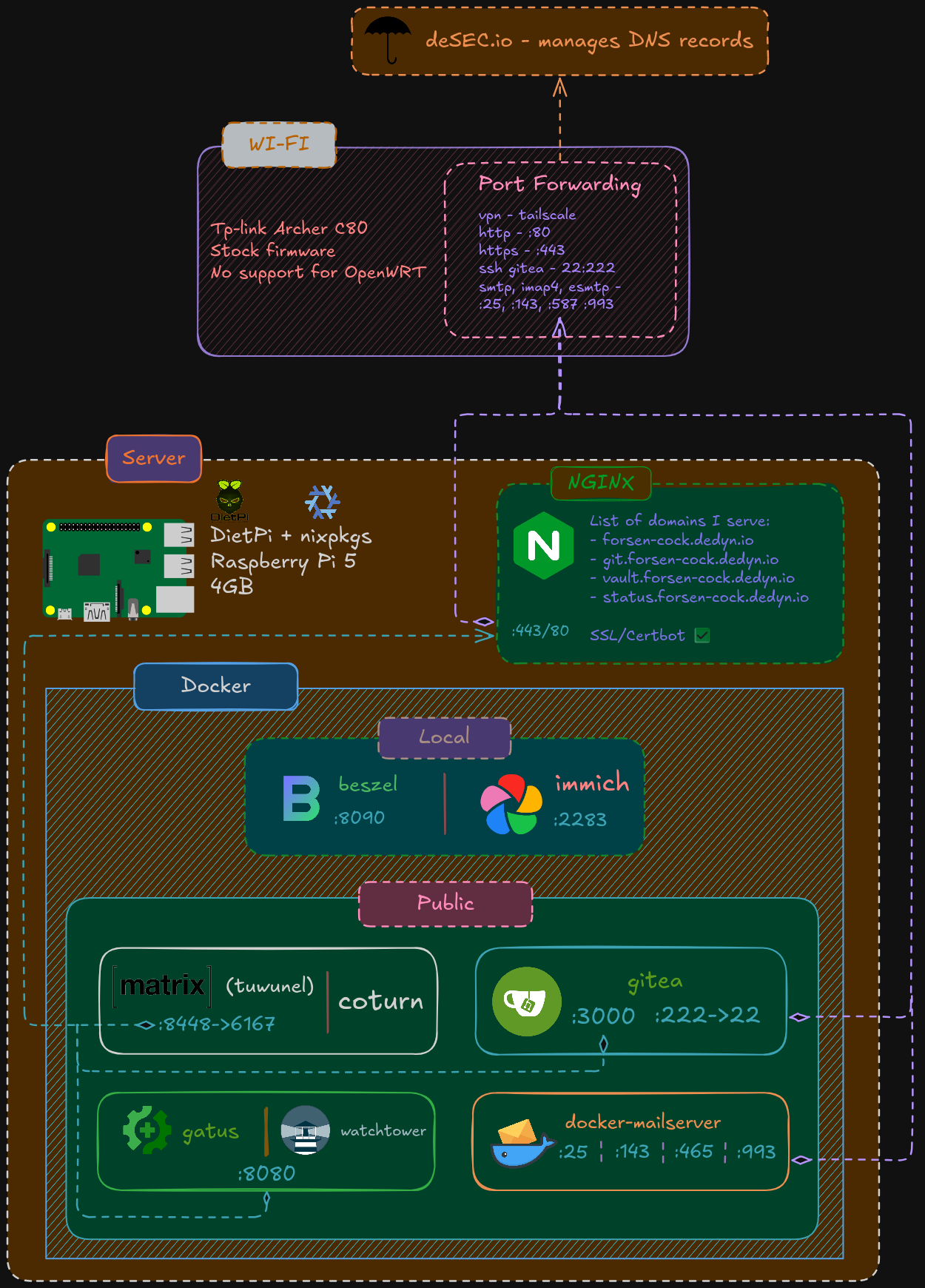
Self-hosting
I have a Raspberry Pi 5 with 4GB of RAM running DietPi and nixpkgs (I hate outdated Debian packages).
Currently hosting a bunch of stuff on it via Docker containers with help of desec.io.
Contact Me
You can reach me via the following channels:
- Email:
amoelle@proton.me | elleoma@forsen-cock.dedyn.io - Matrix:
@elleoma:forsen-cock.dedyn.io - Mastodon: @elleoma@soc.ua-fediland.de
- Twitter: @0xAm03113
- My github: https://github.com/elleoma
My setup
I use Arch Linux on a laptop — it just works and lets me get things done. I run Hyprland and use NVChad for Neovim.
Here’s my fastfetch output:
▄ 💻️ OS info:
▟█▙ ┌────────────────────────────────┐
▟███▙ OS: Arch Linux x86_64
▟█████▙ Kernel: Linux 6.15.9-arch1-1
▟███████▙ Packages: 2103
▂▔▀▜██████▙ Display: 1920x1080@144 Hz
▟██▅▂▝▜█████▙ WM: Hyprland 0.50.1
▟█████████████▙ Terminal: tmux 3.5a
▟███████████████▙ └────────────────────────────────┘
▟█████████████████▙
▟███████████████████▙ ⚙️ Hardware:
▟█████████▛▀▀▜████████▙ ┌───────────────────────────────────┐
▟████████▛ ▜███████▙ CPU: Intel Core i7-12650H
▟█████████ ████████▙ GPU1: GeForce RTX 4060 / Mobile
▟██████████ █████▆▅▄▃▂ GPU2: UHD Graphics
▟██████████▛ ▜█████████▙ GPU1 Driver: nvidia
▟██████▀▀▀ ▀▀██████▙ GPU2 Driver: i915
▟███▀▘ ▝▀███▙ Memory: 5.04 GiB / 15.32 GiB
▟▛▀ ▀▜▙ └────────────────────────────────────┘
My dotfiles are here: dotfiles