~ > whoami
I’m a Ukrainian student and a unix/linux & open-source enthusiast, trying to get into cybersecurity, gain some practical skills.
My interests are:
- Cybersecurity
- Low-level programming: C, Rust, Zig, C++, Assembly
- Reverse engineering (IDA, Ghidra, NinjaBinary)
- Electrical engineering
- PCB designing (KiCad — yet to try)
- Self-hosting
- A little bit of 3D
- A little bit of game development
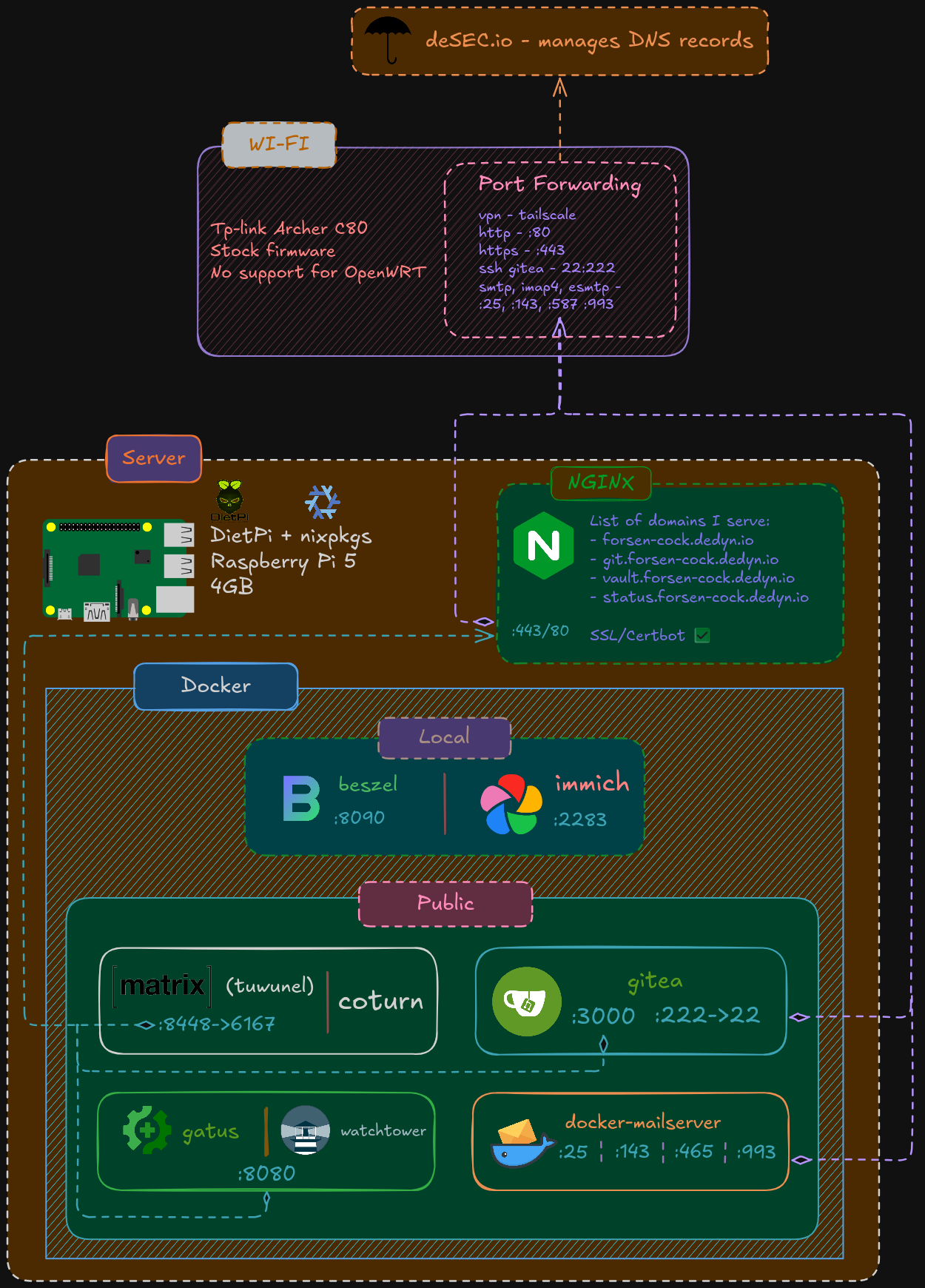
Self-hosting
I have a Raspberry Pi 5 with 4GB of RAM running DietPi and nixpkgs (I hate outdated Debian packages).
Currently hosting a bunch of stuff on it via Docker containers with help of desec.io.
Some project I have
Facinus
Since our college switched from Windows to Ubuntu, I had a cool idea to remotely control my classroom PCs.
I discovered gsocket.io and started developing a tool that deploys a local web admin panel to
collect logs from connected clients.
I used an Ubuntu VM in QEMU and Bash scripted everything with some help of AI.
Cybersecurity
I’ve been into cybersecurity for about 2 years now. I started with the normie setup — Kali Linux dual-booted next to Windows, learning through trial and error.
Eventually I spent more time on Linux, moved to KDE, configured everything myself, riced my terminal. Later switched to Arch and Hyprland.
I still have lots to learn, and I’d love to document all the tools and techniques I come across.
HackTheBox
HTB gave me that initial hands-on boost I needed.As of right now I’ve solved more than 50 boxes (3 of them “Insane”: DarkCorp, Mist, and MassGarden).
Even though I sometimes rely on writeups and walkthroughs, I learn a lot from the infrastructure behind each box.
I’m not sure if using writeups spoils the learning, but for now it gives me clarity and saves time. I aim to shift toward solving without spoilers in the future.
Russian targets
I’m Ukrainian, so I practice skills on real russian infrastructure. It’s morally right and beneficial, especially in these times.
Bug bounty
Bug bounty is fascinating — legally hacking in-scope apps and possibly earning money.
But as a beginner, it’s tough. Recon is time-consuming, and rewards don’t always justify the effort unless you're really skilled.
I’ve tried a few programs but haven't found any serious vulnerabilities yet. I plan to shift my focus toward learning specific attack techniques and improving my skills first.
My setup
I use Arch Linux on a laptop — it just works and lets me get things done. I run Hyprland and use NVChad for Neovim.
Here’s my fastfetch output:
~/shit ❯ fastfetch
OS : Arch Linux x86_64
Kernel : Linux 6.15.5-arch1-1
Display : 1920x1080 @ 144 Hz in 15" [Built-in]
Terminal : tmux 3.5a
CPU : 12th Gen Intel(R) Core(TM) i7-12650H
GPU : GeForce RTX 4060 Max-Q / Mobile
GPU : UHD Graphics
GPU Driver : nvidia (proprietary) 575.64.03
GPU Driver : i915
OS Age : 182 days
My dotfiles are here: dotfiles